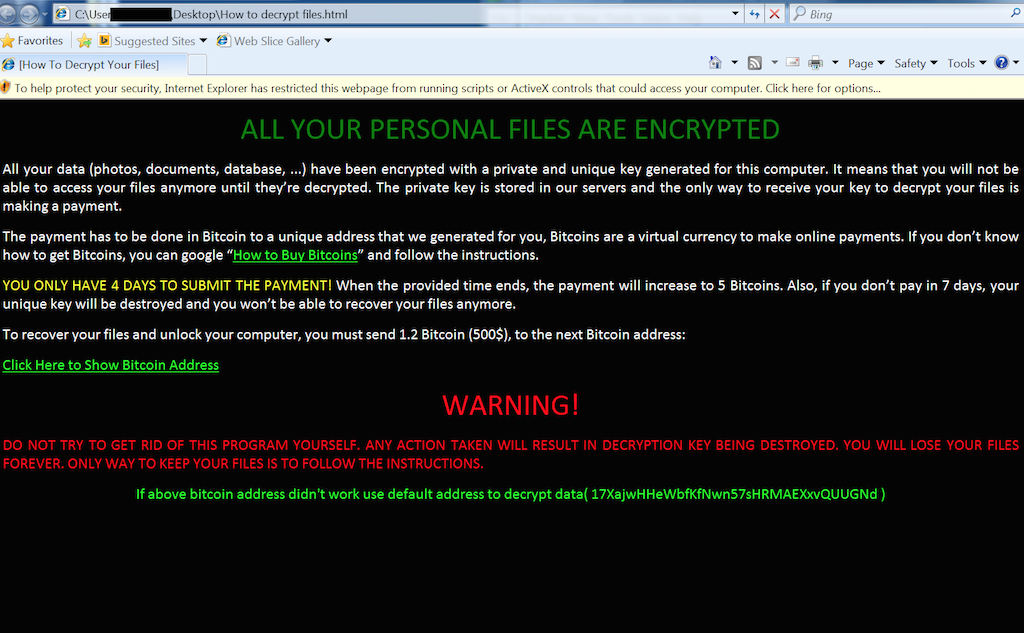
If you have never suffered from a Rasomware on your personal Pc or laptop and you are always online then you are very lucky.
Ransomware is a type of malicious software from cryptovirology that threatens to publish the victim’s data or perpetually block access to it unless a ransom is paid.

Ransomware is a type of malicious software from cryptovirology that threatens to publish the victim’s data or perpetually block access to it unless a ransom is paid.
It actually blocks you from accessing your documents, files, media, apps and software on your computer.
I suffered an ordeal and had to flash my computer losing every single document, media, applications, and software.
Rasomware can be got from clicking on unidentified ads, software download links, random links sent to emails, removable storage devices and others.
There are a number of a million of hackers coming up with Malwares and Ransomwares but here are the common and recent dangerous examples of Rasomwares around the world:
- GandCrab: A new strain of ransomware discovered early in January 2018. The malware demands a cryptocurrency fee for the return of any files. More worrying, GandCrab is being marketed as a ransomware as a service package to budding cyber criminals, who could split the profits with the developers at a ratio of 60:40. Meaning that you distribute the malware and when the victim pays you are given 40% of the initial Rasom.
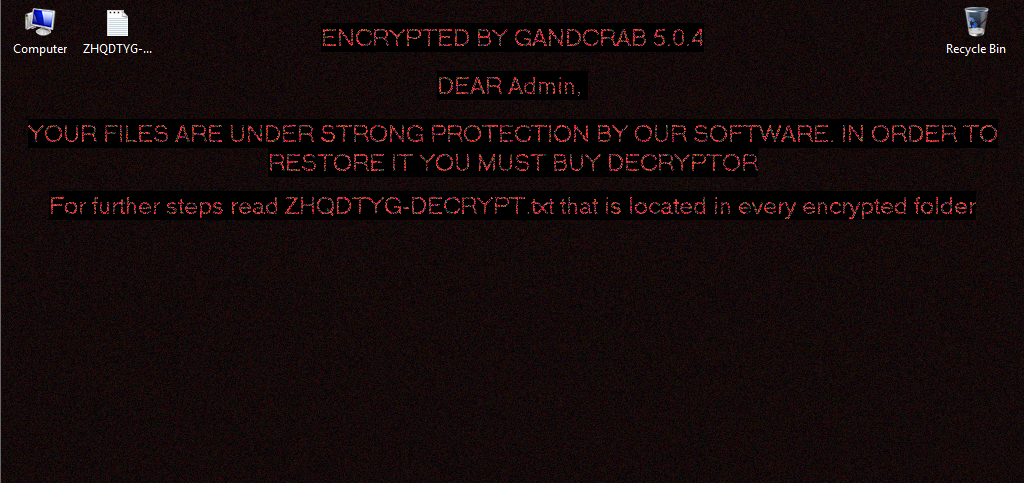
More worrying, GandCrab is being marketed as a ransomware as a service package to budding cyber criminals. Internet photo
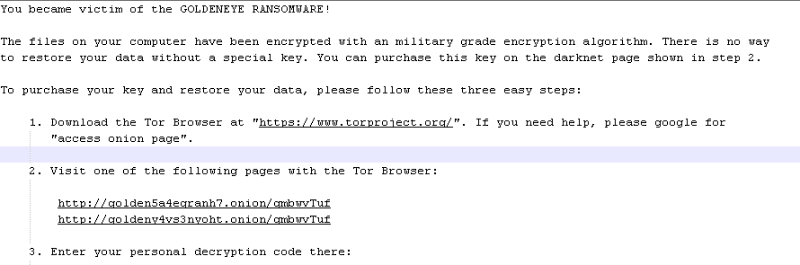
- GoldenEye: The ransomware attacks were reported in Ukraine, it hit the national bank, state power company and Kiev’s largest airport on June 27, 2017, which is thought to be a mixture of Petya and another ransomware, called Mischa. GoldenEye will prevent computer systems from being booted up and from victims retrieving any stored data. When the user reboots, instead of Windows they could see a skull and crossbones splash screen with a ransom demand.
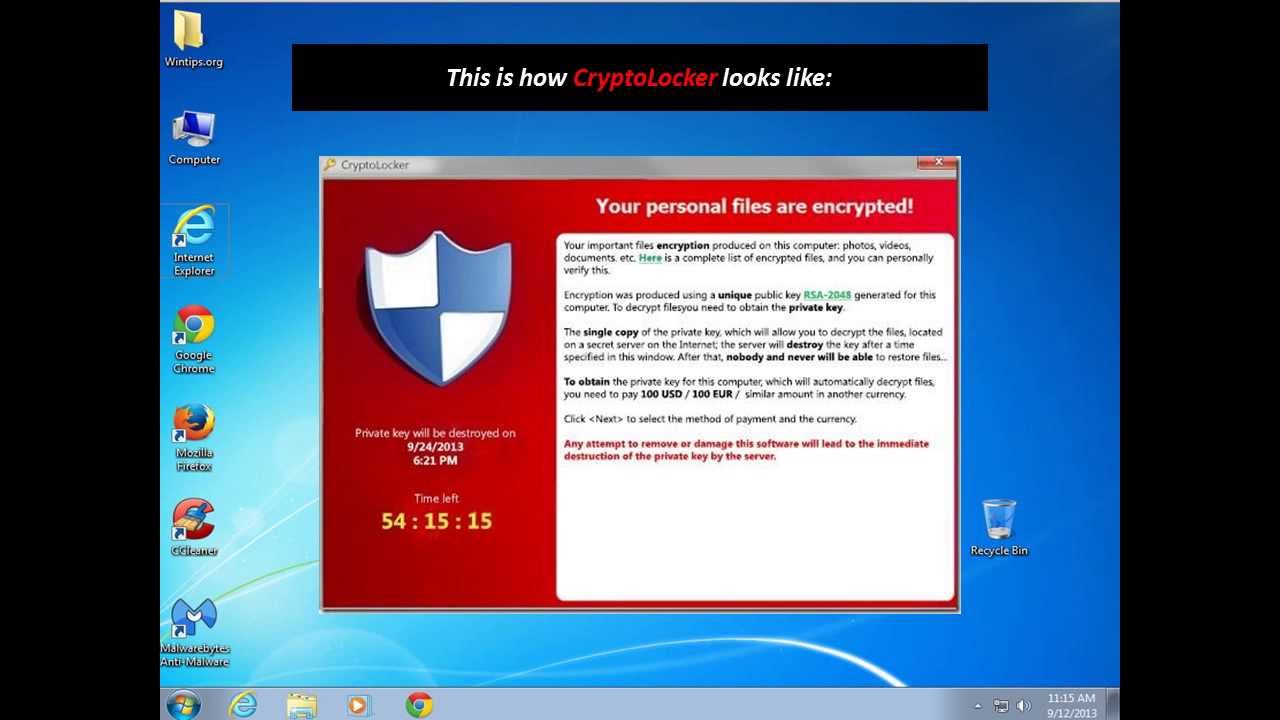
- CryptoLocker: Long gone but it deserves disapprobation because its peak in 2013 proved to cyber criminals how successful ransomware could be.
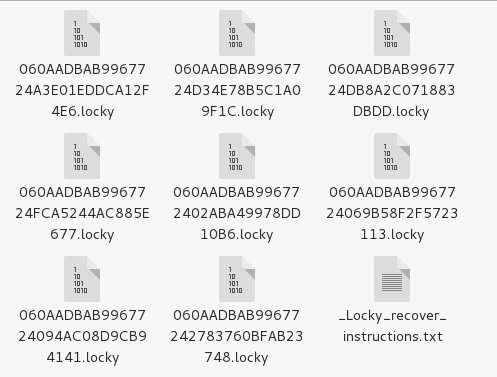
- Locky: Locky is as bad as ransomware can get. Locky’s creators seem to have thought of everything, not only encrypting a wide range of data files but even Bitcoin wallets and Windows Volume Snapshot Service (VSS) files in case users try and restore files using that. It reaches out to attached shares and even other PCs and servers. It uses strong encryption and has found several high-profile victims.
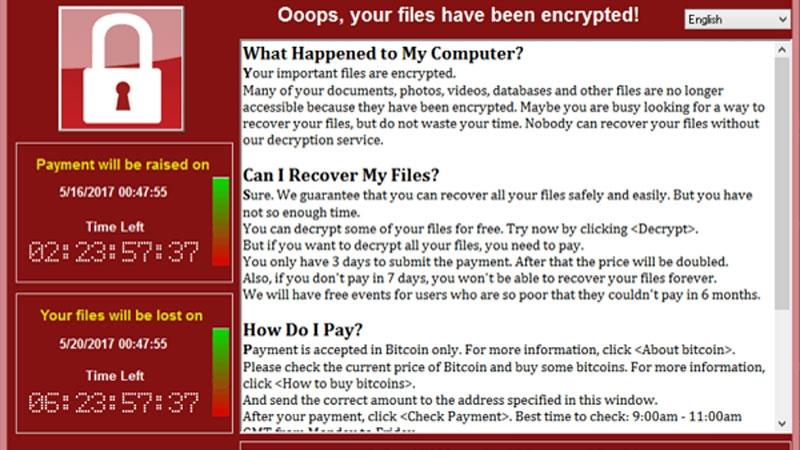
- WannaCry: EuroPol has described the WannaCry ransomware, which shut down hospital infrastructure all over the UK and uses a leaked exploit first developed by the National Security Agency, as unprecedented in scale.
- VCrypt: ZCrypt tries the unusual technique of spreading as a virus. This means that it doesn’t rely on malicious emails to find victims and can spread on USB sticks.
But the Cry is almost over because as Hackers generate more torture chambers on peoples Pcs, Developers are also working Tooth and Nail to over come people’s miseries.
The Romanian Police in collaboration with Bit defender and Europol have developed project “No More Ransom.” The project released an updated and more potent decryption tool for the GandCrab ransomware in what Europol has described as the “latest victory of law enforcement in the battle against ransomware.”
The decryption tool was developed by Romanian Police, Europol, and Bitdefender, and will be made available on the No More Ransom project website for download.
The tool is an update on a first version that was released in February by Bitdefender. The new GandCrab decrypter is more potent and can recover data for more GandCrab versions –v1 (GDCB extension), v4 (KRAB extension), and v5 (random 10-character extension, also the current/latest GandCrab version), respectively.
The new decrypter also comes after Bitdefender released a more limited decryption tool earlier this week for GandCrab ransomware victims located in Syria. The Romanian antivirus maker was able to create that decrypter after the GandCrab developer released legitimate and authentic decryption keys for victims located inside Syria, out of compassion.
In a blog post, Bitdefender said they’re still working on creating a decrypter that can unlock files encrypted by GandCrab versions 2 and 3.
A representative of the Romanian Police Central Cybercrime Unit didn’t comment on the operation’s particularities, citing an ongoing investigation, but told ZDNet the new decryption tool was “a cryptographic issue rather than an infrastructure issue,” suggesting investigators found a flaw in GandCrab’s file encryption routine. Flaws in ransomware encryption schemes is how authorities and cyber-security firms have been able to decrypt most ransomware strains in the past years.
The new GandCrab ransomware decryption tool is indeed a great victory for law enforcement, and indirectly victims who had their files encrypted. While GandCrab v1 was mostly deployed in January and February, v4 and v5 have been put in circulation in July and September, respectively. This means that anyone infected with GandCrab versions released in the past four months can now recover files for free, without paying GandCrab’s ransom demand –which usually varies from $600 to $3,000 per infected computer.
GandCrab is, by far, the most active and widespread ransomware strain today, taking the place of Locky and Cerber, the leading ransomware strains of 2016 and 2017.
The GandCrab ransomware is developed by a central figure who goes by the name of “Crab” or “Gandcrab” and rented to other cybercriminals on a well-known hacking forum.
Its RaaS (ransomware-as-a-service) model allows distributors to keep 70 percent of the ransom payments, while Crab takes a 30 percent cut, although Crab used to take a smaller percentage when the ransomware first launched in January.

The decryption tool was developed by Romanian Police, Europol, and Bitdefender, and will be made available on the No More Ransom project website for download.
IT experts and Developers recommend the following to avoid being a victim of Rasomware, Malware and Cyber attacks:
- Back up all information every day, including information on employee devices, on offline and offsite location. So you can restore encrypted data if attacked.
- Norton Anti Virus Developers advice that do not pay the ransom. It only encourages and funds these attackers. Even if the ransom is paid, there is no guarantee that you will be able to regain access to your files.
- Restore any impacted files from a known good backup and this Backup is to be done everyday so that if you are attacked the best option is to Format all Hard disks and registries and reinstall your system and restore your data again. Restoration of your files from a backup is the fastest way to regain access to your data.
- Do not provide personal information when answering an email you are not sure that it is secure, unsolicited phone call, text message or instant message. Phishers will try to trick you or company employees into installing malware, or gain intelligence for attacks by claiming to be from IT. Be sure to contact your IT department if you or your coworkers receive suspicious calls about computer systems.
- Use reputable antivirus software and a firewall. Maintaining a strong firewall and keeping your security software up to date are critical. It’s important to use antivirus software from a reputable company because of all the fake software out there.
- Do employ content scanning and filtering on your mail servers. Inbound e-mails should be scanned for known threats and should block any attachment types that could pose a threat.
- Do make sure that all systems, including operating systems, applications. and software are up-to-date with relevant patches. Exploit kits hosted on compromised websites are commonly used to spread malware. Regular patching of vulnerable software is necessary to help prevent infection.
- If traveling, alert your IT department beforehand, especially if you’re going to be using public wireless Internet. Make sure you use a trustworthy Virtual Private Network (VPN) when accessing public Wi-Fi.
- Keep clear inventories of all of your digital assets and their locations, so cyber criminals do not attack a system you are unaware of.
- Segment your network: Don’t place all data on one file share accessed by everyone in the company.
- Train staff on cyber security practices, emphasizing not opening attachments or links from unknown sources.
- Develop a communication strategy to inform employees if a virus reaches the company network.
- Before an attack happens, work with your board to determine if your company will plan to pay a ransom or launch an investigation.
- Perform a threat analysis in communication with vendors to go over the cyber security throughout the lifecycle of a particular device or application.
- Instruct information security teams to perform penetration testing to find any vulnerabilities.
- Last but not least Please avoid opening ads from unknown sites, opening downloading any apps or softwares from unrecognized or not recomemded sites and don’t not download software cracks and Keys from any site other than the official site of that particular Software.
Content from various Cyber security Sites.